Peter Sunde, co-creator of Njalla, created a Twitter thread explaining how the domain dark.fail (@DarkDotFail) got hijacked from Tucows and then moved to Namecheap.
Njalla revealed yesterday that Tucows was the victim of a phishing attack that affected some domains registered with Njalla and other resellers and registrants. Tucows received a (fake) court order (including a gag order) to hand over a set of domains, where some where registered through Njalla (and others weren’t).
Maybe you heard that the domain https://t.co/3Ip8qhGgxd (@DarkDotFail ) got hijacked. Here’s the story on how it happened. A thread! (I’ve pieced together the data I have so I might have some small errors in this thread, FYI.)
— Peter Sunde Kolmisoppi (@brokep) May 3, 2021
Njalla is a Tucows domain name reseller as Njalla is not yet a registrar for legacy and New gTLDs. ICANN has refused to give Njalla a registrar accreditation. (Read more here and here.)
(You can read more about the Njalla privacy domain registration service here.)
Here is the complete story as told by Peter Sunde:
Maybe you heard that the domain http://dark.fail (@DarkDotFail) got hijacked. Here’s the story on how it happened. A thread! (I’ve pieced together the data I have so I might have some small errors in this thread, FYI.)
First, the domain was registered through a service I started, @njal_la (or transferred in, not sure here). Njalla in turn uses @tucows as a registrar for .FAIL domains.
On the 28th of April, Tucows receives a court order, from Amtsgericht Köln, the district court of Cologne, NRW, Germany. It contains a list of domain names that they want handed over. Two of three domains listed are registered through Njalla, the last one with @hover.
The PDF looks like a real court order, I’ve seen a lot of these (…) but this one is fake. It’s without spelling errors, referring to a German paragraph that was previously used to get the domain http://kino.to suspended. So really looks legit.
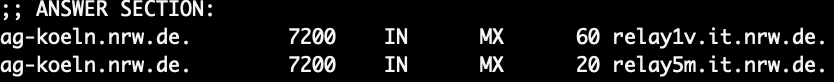
I do not have a copy of the email and headers, but I’m assuming it is sent using a sender from the domain listed in the document, agkoeln-nrw[.]de. The official domain for Amtsgericht Köln is ag-koeln[.]nrw[.]de. I.e. Not the same.
If you go to the listed domain, agkoeln-nrw[.]de, you will be redirected to the correct domain.
If you look at the MX pointers for the domain, it points here:
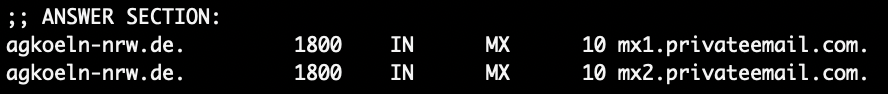
Whereas the correct MX pointers for the correct Amtsgericht Köln is:
The phishing domain is registered with @Namecheap, and is also using their web redirect service and their email service.
Now, Tucows probably deals with quite a load of court orders, and sloppily let’s this one through. It looks convincing, the domain is almost correct and if they tried browsing they would have ended up on the correct site. It’s a classic phishing expedition.
The fake court order also included a gag order, to not inform the registrant that this was happening. This means that neither Njalla nor Hover was informed about what was going to happen and had no possibility of stopping the transfer.
We presume that Tucows replied with the transfer codes for the domains to the phishing email. We have asked them for more information (like a full copy of the incoming email with SMTP headers etc) and hope to get that soon.
Very quickly after that happened, the domains were transferred out from Tucows. One of the Njalla-originated domains went to @EpikDotCom
and another one to, you guessed it, @Namecheap.
It didn’t take long until the websites of the domains (and their MX pointers) all of a sudden had new content. The new sites are now phishing sites, and most likely making a lot of money and collecting sensitive user data.
Njalla (and presumably Hover) informed Tucows very quickly and they were to their credit very quick to put a lot of effort into solving the situation, and they put (from our experience) their best people on it.
Now, I don’t like @EpikDotCom from a personal and political standpoint. But credit due: when they were informed about the phishing situation, the domain that was transferred to them was handed back very quickly all things considered.
Now, the dark[.]fail domain is another story. There’s been a lot of effort put in from the registrant, the reseller, the registrar and many others to return the hijacked domain. But the gaining registrar, @Namecheap, has still not done anything at all.
We’ve all asked if they could first of all suspend the domain so that the active phishing site (yes, it’s insanely enough still active, visit with caution) would be stopped. And the domain should be returned, as per regulation that Namecheap has agreed to with ICANN/registry.
Njalla has even contacted @DonutsInc that operates the TLD .fail in order to actually get the site shut down and the domain returned. Hopefully this will amount to enough pressure to make @Namecheap actually rectify the situation.
(Personally I even contacted The @NamecheapCEO who has still not returned my e-mails.)
Now, here’s the kicker. Today we got informed that @Namecheap doesn’t agree that the court order is fake! Even though the domain listed on the court order is registered through them, the web redirect is hosted with them, and the incoming email is hosted by them.
So even though @Namecheap has all the evidence needed to stop not only one but two ongoing phishing attacks (the domain hijacked plus the domain used to do it) hosted by them, they refuse.
The past days has not been great for Tucows nor the people working with them. It was a human error, and unfortunately out of the hands of Njalla (& hover). If the court order would have ended up with Njalla, I’m 110% certain it would not have happened.
I’ve seen a few people very upset with Njalla for “shitty security”. The way that domain names work (with this hierarchy) it’s near impossible to optimise this flow. Believe me; I’m trying. I left @njal_la (I’m on the advisory team still) to work on a new registrar!
My registrar is focused on better technology, and a lot more security. However, ICANN refused me to do so. Ironic.
So if ICANN had not refused me – afraid that I would not follow their regulation – we would not have ended up in a situation where a domain was phished because of low opsec by one ICANN accredited registrar, and then not returned because another is breaking ICANN regulation.
Some of the privacy sensitive domains that used Njalla decided to move. All respect to that. Some have moved to other Tucows-partners (…) and some of them moved to, you guessed it, @Namecheap . Oh do I wish I would had an alternative for them for .fail domains.
Now, the phishing attack is still ongoing, and if enough people would push @Namecheap and their @NamecheapCEO on social media, maybe they will help @DarkDotFail out and get their domain back. Thanks.
BONUS 1: The court order PDF has no metadata. It’s written in German with correct spelling, the person processing it at Tucows speaks German.
BONUS 2: The domains transferred to @Namecheap use their privacy service — would say uncommon for a court to do.
BONUS 3: If @Namecheap is claiming the court order is correct, they must believe that the German court has themselves put up a phishing site.
BONUS 4: The domain transferred to @EpikDotCom listed NRW as the region of the registered name holder in the whois data. Most likely the account created there was registered to match the transfer in? Maybe you can update us Epik?
BONUS 5: The domain that was with @hover seems to also be stuck with @Namecheap.
BONUS 6: The court order makes me believe that the attacker is _very_ well versed in how these court orders usually look, and have directed it extremely well within Tucows. It’s not someone without insight.
Also want to add, this is how @njal_la deals with fails, not just .fail domains, but our own fails: we’re transparent and disclose what we can.
Oh man. We just got another e-mail from @Namecheap a few minutes ago. “Unfortunately, we failed to locate any phishing-related content on the reported domain.”
Not sure how they could read our abuse report, since they appear to be totally blind!
FINALLY!! From @Namecheap:
“Please be informed that the http://dark.fail domain was disabled. We would like to note that the website could not be treated as a phishing one because it did not contain fields to enter sensitive data.” Now we just need them to send it back.
UPDATE: Finally the domain name dark.fail was returned to its owners:
We got our domain https://t.co/vdpHwXeqt3 back!! Massive THANK YOU to @njal_la, @brokep, and all who supported us over the past four days while a phisher hijacked and operated our clearnet site. Rebuilding carefully.
— dark.fail (@DarkDotFail) May 4, 2021
 OnlineDomain.com Domain Name News & Opinions
OnlineDomain.com Domain Name News & Opinions




 OnlineDomain.com - © Copyright 2012-2025 - All Rights Reserved
OnlineDomain.com - © Copyright 2012-2025 - All Rights Reserved
So all we have to do is register FB-I.ORG and we can request the transfer of domains and the contents of your bank account while at it.
One of the latest type of hacks by our friends in Russia is to hack sites for samples of correct paperwork.
When you get a legal summons you had it to a lawyer, then if they screw up you can sue them for negligence.
All you had to do was put the URL into pingdom tools and you would have seen the redirect in the waterfall.
Obviously it is easy with hindsight but the highest level of checking should be used.
Also any document that tells you not to do things or gives you a time limit should make you suspect.
What would have been the worst case had you simply said “we have passed this to our Lawyers and they will be in contact with you”.
Do you have any idea how slow the Police are on legit issues.
Hopefully registrars can learn from this cock up.
Well informed article. If there is any court ruling it must have been listed on German court site as well. Namecheap must be asked to look at it.
I believe namecheap only proactively works for rich people. Remember how in my case against brent Oxley they almost got ready to file transfer dispute resolution process even though cost for it is quite high and the matter was and is still pending in indian courts.
Do namecheap has someone inside their company helping the hijacker. Are they too ignorant to even acknowledge the fake court order. I salute to epik to do the correct thing.