Spamhaus issued its botnet threat update for Q2 2020.
“The pandemic certainly didn’t put the brakes on botnet operators in Q2 2020. Unfortunately, they were back in full swing, with a 77% surge in the number of botnet Command & Controllers (C&Cs) tracked and listed by the research team.”
Here is what the Spamhaus report says about the most abused extensions and registrars in Botnets:
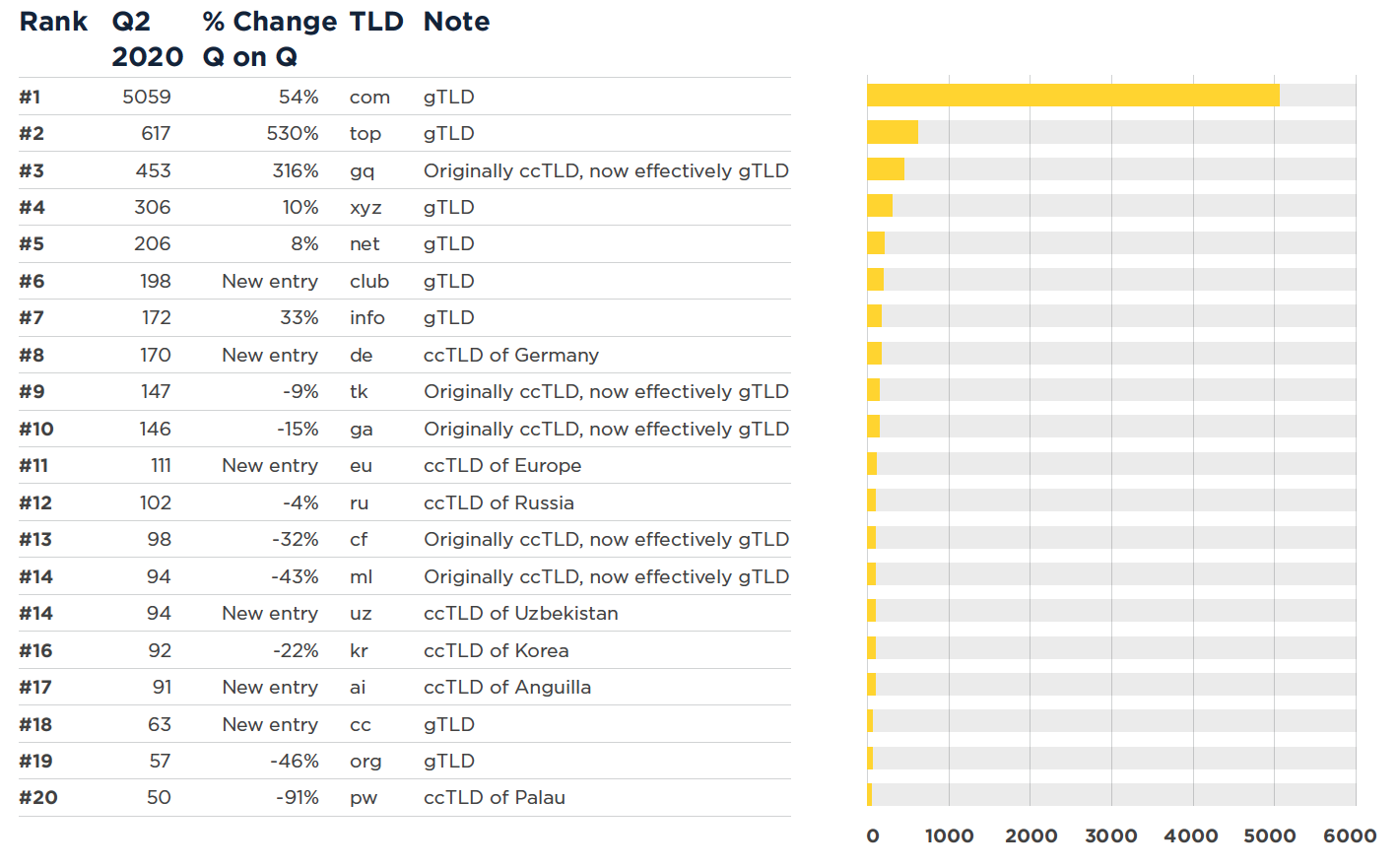
Most abused top-level domains in BOTNETS, Q2 2020
Here are the top-level domains (TLDs) chosen most frequently by botnet operators to host their infrastructure on. There have been significant changes in these between the two quarters, with six new entries and one meteoric rise.
.top & .gq Having sat in the lower part of the Top 20 List in Q1, .top, has seen an extraordinary 530% increase in Q2 to take it into second place, behind .com. Another TLD which has seen huge increases between the two quarters is .gq, with a 316% increase.
.pw With a 91% decrease in associated botnet traffic .pw has dropped from #3 in Q1, to #20 in Q2.
.de The country code top-level domain (ccTLD) of Germany, .de, has been listed for the first time in our Top 20 list.
Top abused TLDS – number of domains
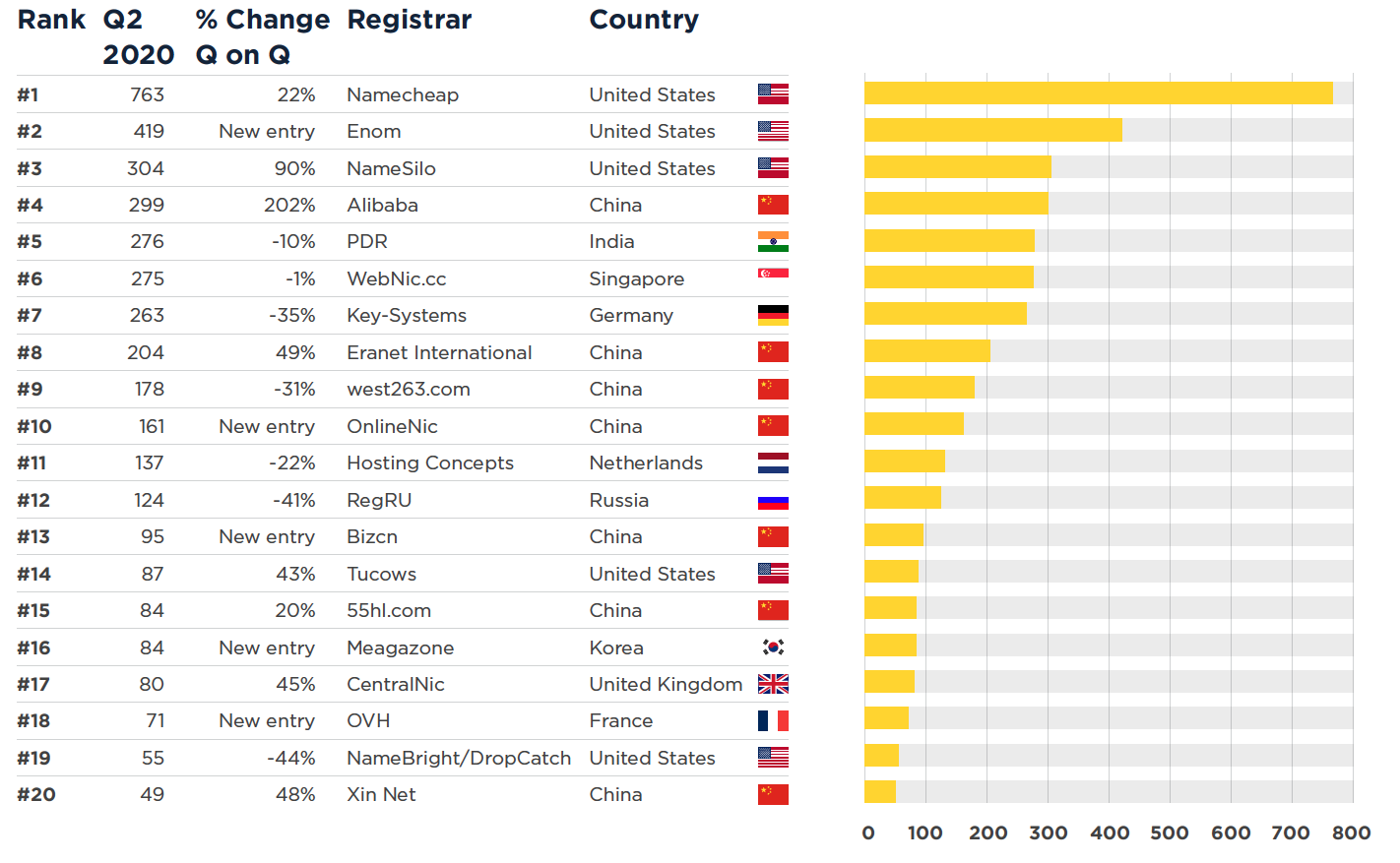
Most abused domain registrars in BOTNETS, Q2 2020
When setting up a botnet C&C infrastructure, threat actors need to decide who they are going to register their domain with. Registrars can’t easily detect fraudulent sign-ups; however, domains used for botnet C&Cs don’t tend to have a long lifespan with well-run registrars.
Namecheap The US-based domain registrar Namecheap has been in the #1 spot for a significant length of time.
Enom Entering the Top 20 at #2, Enom had 419 botnet C&Cs operating on domains registered to it in Q2.
Highest climbers NameSilo had a 90% increase in the number of botnet C&Cs operating on domains registered through them in Q2, taking them to #3 on the Top 20 List. However, with an even more considerable increase of 202%, was Alibaba, moving up #11 in Q1 to #4 in Q2.
Most abused domain registrars – number of domains
 Read here the complete Spamhaus report.
Read here the complete Spamhaus report.
 OnlineDomain.com Domain Name News & Opinions
OnlineDomain.com Domain Name News & Opinions


 OnlineDomain.com - © Copyright 2012-2026 - All Rights Reserved
OnlineDomain.com - © Copyright 2012-2026 - All Rights Reserved