It has been more than a year since Tucows launched the Tiered Access Compliance & Operations portal, sometimes called “Gated Whois,” and it’s been around six months since they shared their first set of statistics on how and by whom this platform is being used. The latest update brings Tucows statistics current through mid-October 2019. This data provides insight into how Tucows handles requests for non-public personal data.
It’s important to remember that these statistics represent disclosure requests by a third party asking for personal data which is not publicly available. Each request is examined by a member of the Tucows legal team, who reviews the request and decides what data, if any, should be disclosed based on applicable law and registrar ICANN obligations.
Here is the Tucows report:
Data disclosure requests
We received 467 requests for data in the period from February to mid-October 2019 and 2617 requests total to date.
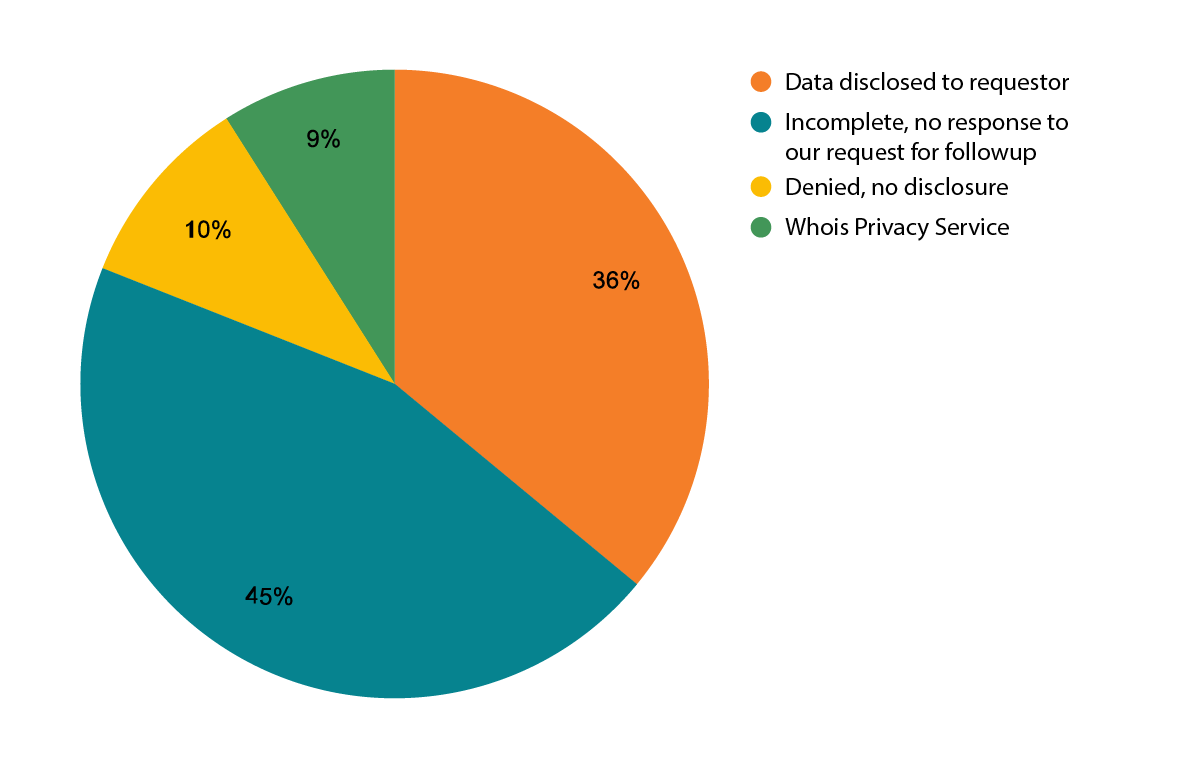
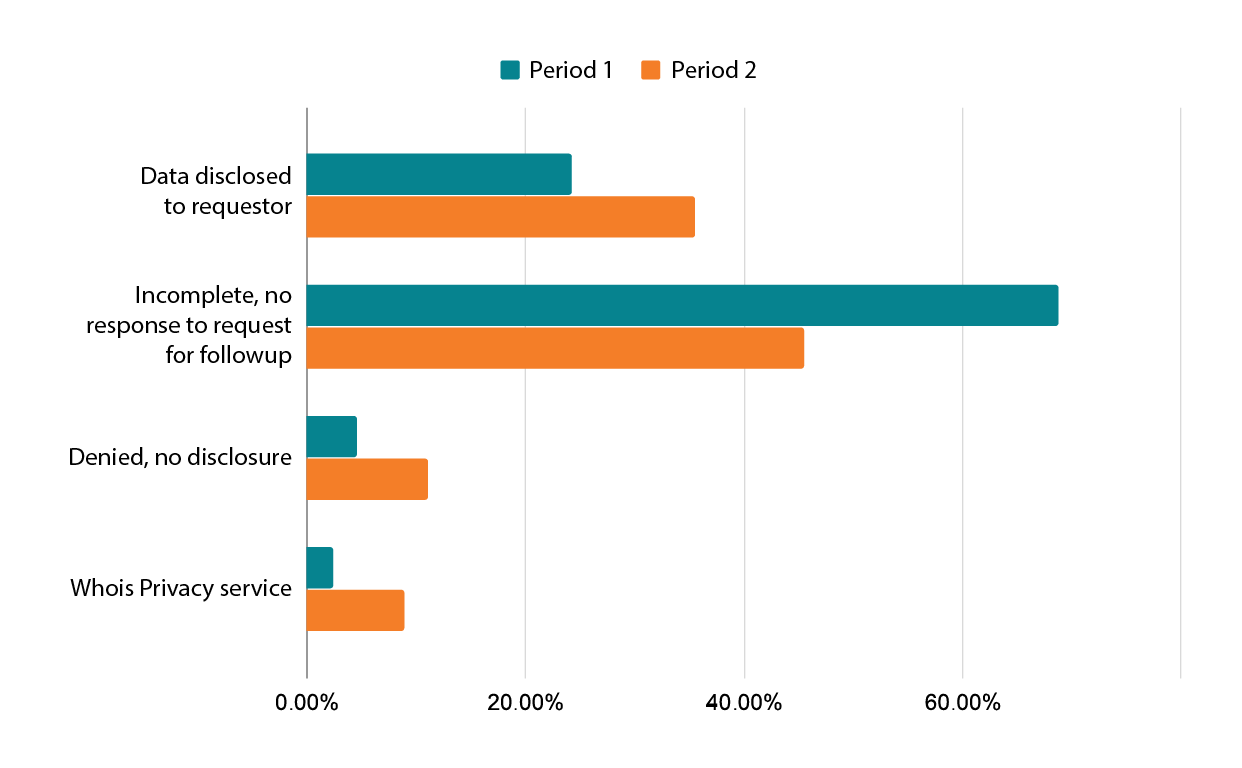
- 36% of requests received in this period resulted in registration data being disclosed to the requestor
- 45% were incomplete and the requestor did not respond to our followup for further information, so no data were disclosed
- 10% were denied, following a determination that the requestor did not have an adequate lawful basis
- 9% of requests resulted in “disclosure” of Whois Privacy information—that is, the same information already publicly available to a requestor
Disclosure request outcomes – Period 2
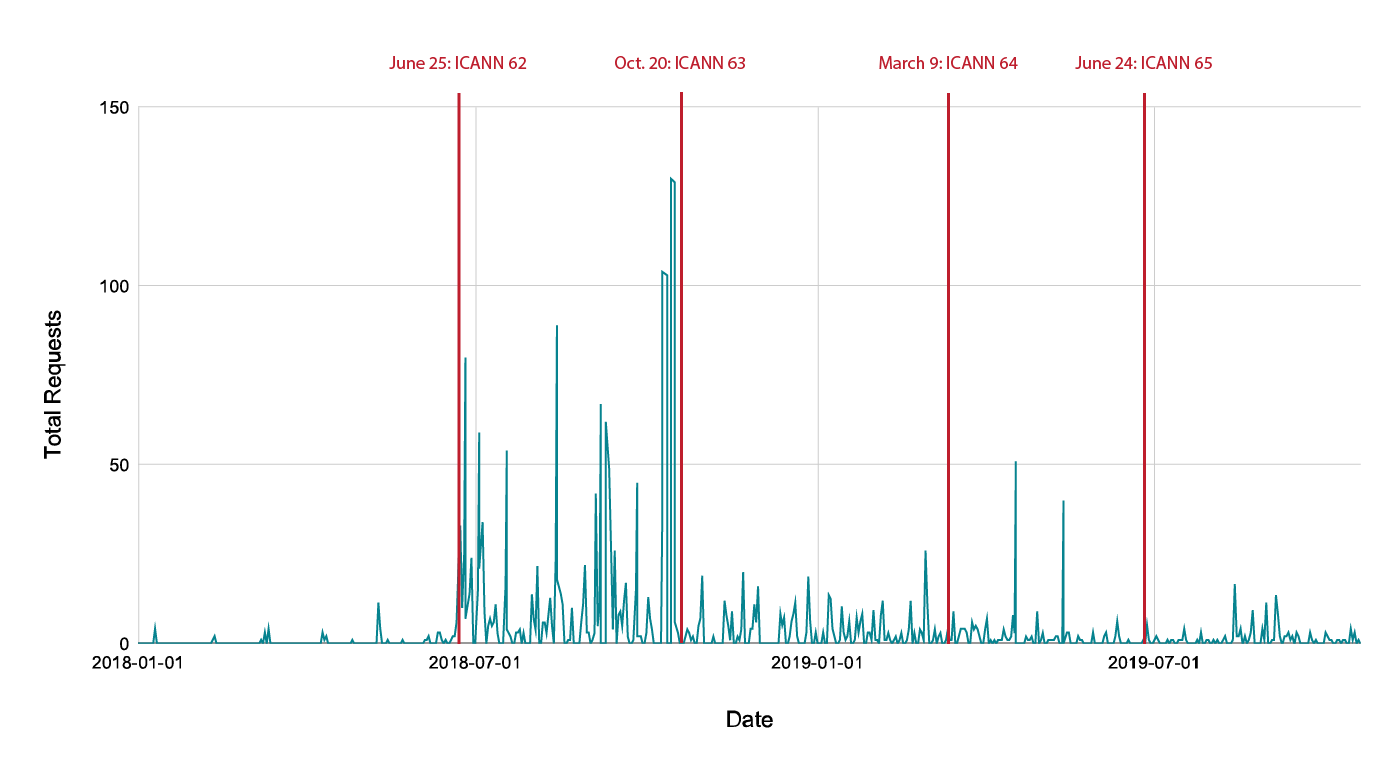
 We are pleased to note that we did not find significant spikes in requests during this reporting period, unlike our previous report where request volumes increased around ICANN meetings, suggesting that some portion of those requests were submitted in order to skew the data towards an argument that disclosure requests are not being processed in a timely or appropriate manner.
We are pleased to note that we did not find significant spikes in requests during this reporting period, unlike our previous report where request volumes increased around ICANN meetings, suggesting that some portion of those requests were submitted in order to skew the data towards an argument that disclosure requests are not being processed in a timely or appropriate manner.
Here’s an illustration of the volume requests over time since we’ve launched Tiered Access:
Compared against our last report
Perhaps more interesting than the overall numbers is how the current reporting period compares to the previous one: comparing request and response statistics as users become more accustomed to the new system and have learned how to effectively request data; the comparisons below are percentages.
Disclosure request outcomes compared
- Increase in disclosure of non-public data from 25% to 35% and decrease in incomplete requests from 69% to 45%
These changes are likely a result of our efforts to work with high-volume requestors to improve the quality of their requests - Increase in denied requests from just under 5% to just over 11%
We attribute this to small-volume and single requestors who recently discovered our Tiered Access portal and do not yet understand how to submit a request that allows us to adequately evaluate their legitimate rights against the privacy rights of the registrant. We will work to better describe the request process at the point of access. - Increase in requests for data where the domain has Whois Privacy enabled from 3% to 9%
When a domain uses one of our Whois Privacy services, we instruct requestors to submit legal process before disclosing the underlying personal data. We also, however, provide the privacy data, as the email address can be used to contact the registrant directly.
Duplicate requests
We continue to see a significant rate of duplicate requests. These include requests from the same source and from multiple requestors, each purporting to represent the same interests. When we receive a second request from the same requestor, we refer them to our prior correspondence—whether that included a request for more information (most often the case) or disclosed personal data. When we receive a request for the same domain’s data from a different party, we encourage the two parties to work together to determine which one represents the legitimate purposes for the data disclosure. We do this whether the data were previously disclosed or not.
As before, a statistically-significant amount of all requests come from the same single requestor mentioned in our previous report; this is the largest individual requestor using our Tiered Access system. However, their requests have dropped by half—last time we shared stats, this requestor represented nearly 65% of all requests, while for period 2 they make up 30% of all disclosure requests submitted to our Tiered Access system. We have worked with this requestor to refine and improve the quality and type of their requests, which has resulted in a decrease both in requests sent and requests denied.
Although it makes up only a very small percentage of overall requests (1.5%), requests for access to our entire registration database have doubled from period 1 to period 2. The majority of these types of requests come from security researchers.
Who wants data?
As stated above, users of our Tiered Access Compliance & Operations system are vetted by our legal team, and disclosure is limited to those with a demonstrated legitimate legal interest. There are a few broad categories of requestors who typically have a legitimate purpose that would allow us to disclose the data—for example, while we do receive requests that are unsolicited offers to purchase a domain, this is not a legitimate purpose for disclosure, as there are other ways to accomplish the same goal without necessitating disclosure of personal data.
The main tracked requestor types are “commercial litigation”, who need access to personal data in order to bring a legal claim of rights against the registrant; law enforcement, carrying out an investigation or in the course of their work; and security researchers, who use certain aggregate data to identify trends in digital abuse. In the chart below, “other” indicates all other requestors, including Certificate Authorities, resellers, and unaffiliated individuals.
Requests by Requestor Type
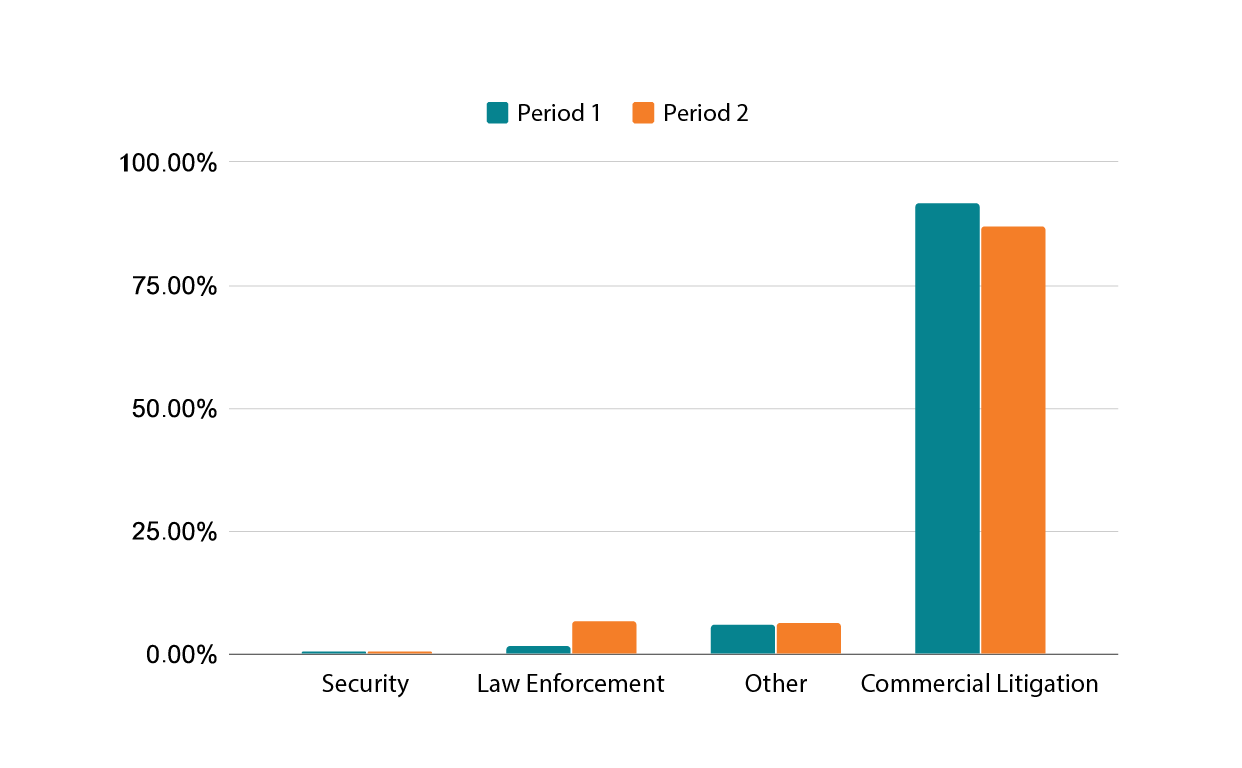
Despite recent concerns raised by security researchers—who comprise the bulk of requests for access to our entire database—the significant majority of all disclosure requests continue to come from commercial litigation interests. We continue to work with security researchers to develop ways for them to access the information they need while protecting the personal data of our customers.
Since law enforcement historically had unrestricted access to the entire registration database, when a law enforcement officer from a jurisdiction we operate in indicates a need for data that would previously have been public, we do disclose the data to them. Law enforcement officers from other jurisdictions must still show legitimate purpose.
Ongoing work
The attitude we have seen throughout this process indicates a culture of entitlement to private personal data and a frustration about the requestor’s obligation to prove that they have a legitimate basis to access personal registrant data.
In February 2019, the Registrar Stakeholder group published recommended minimum requirements for requesting non-public registration data. This valuable resource has been slow to gain traction in the community of requestors, though we continue to educate requestors individually. Our follow-ups, asking for information sufficient to show legitimate purpose, continue to be ignored, indicating to us that our responses to disclosure requests are unmonitored and that those disclosure requests themselves may be spurious or automated.
We work on an ongoing basis both with trade groups and individual requestors to emphasize the importance of balancing rights—the requestor’s right to personal data necessary to defend their legitimate rights against our customers’ right to privacy. Our work includes participation in the EPDP, an effort at ICANN to solidify the rules surrounding how disclosure of personal data should proceed.
We believe that we have developed a viable disclosure model—an opinion shared by trade groups who have indicated that the Tucows Tiered Access Compliance & Operations platform is an industry standard—and are happy to share additional details with other data custodians and with requestors to improve and harmonize the process across the industry. I will be at ICANN 66 in Montreal and available to discuss.
 OnlineDomain.com Domain Name News & Opinions
OnlineDomain.com Domain Name News & Opinions



 OnlineDomain.com - © Copyright 2012-2026 - All Rights Reserved
OnlineDomain.com - © Copyright 2012-2026 - All Rights Reserved
Do they let the person whose data was requested know who and why requested it? Must be a rhetorical question.
I highly doubt it.
This was an ICANN/IP plot from the beggining so they can circumvent police/courts and get access to registrar data easier.